In today’s digital landscape, cybersecurity isn’t just a buzzword; it’s a necessity. We’re constantly bombarded with news of data breaches and sophisticated cyberattacks. So, how do you ensure your organization is truly protected? The answer lies in proactive measures like pentesting and security audits, and understanding the roles of Red and Purple Teams. Let’s explore how these strategies can fortify your defenses in 2024.
Understanding Pentesting and Security Audits
What exactly are pentesting and security audits? They’re both crucial components of a robust security strategy, but they approach security from different angles. Think of a security audit as a comprehensive health check for your entire IT infrastructure. It’s a systematic evaluation of your security policies, procedures, and controls to identify vulnerabilities and ensure compliance with industry standards.
Pentesting, on the other hand, is more like a targeted stress test. It involves ethical hackers (or “pentesters”) simulating real-world attacks to uncover exploitable weaknesses in your systems. It’s a hands-on approach that reveals how an attacker could potentially compromise your defenses.
Why are Pentesting and Security Audits Important?
Simply put, they help you identify and fix vulnerabilities before malicious actors can exploit them. They provide valuable insights into your security posture, allowing you to prioritize remediation efforts and allocate resources effectively. Consider these benefits:
- Identify security weaknesses
- Improve security posture
- Meet compliance requirements
- Reduce the risk of data breaches
- Enhance incident response capabilities
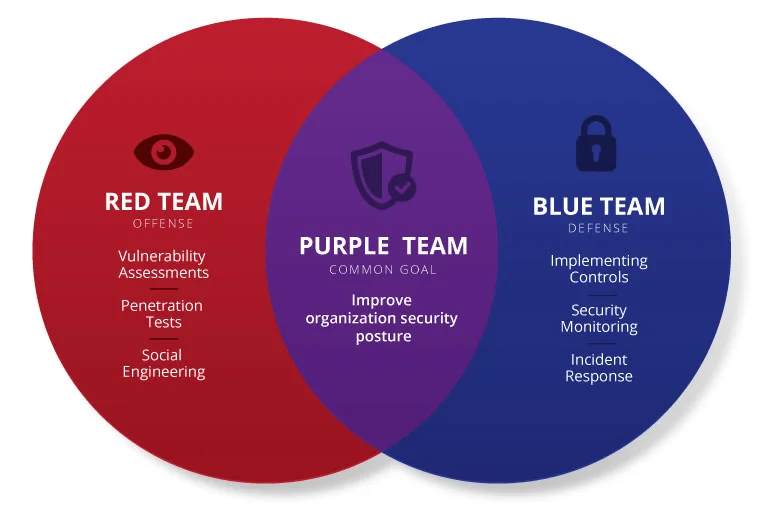
The Role of the Red Team in a Pentesting Security Audit
The Red Team is your offensive security force. Their mission? To think like a hacker and find ways to break into your systems. They employ various techniques, from social engineering to exploiting software vulnerabilities, to simulate a real-world attack scenario. They are relentless in their pursuit of weaknesses.
How the Red Team Operates
The Red Team typically operates with minimal knowledge of your internal security controls. This “black box” approach forces them to rely on publicly available information and their own ingenuity to identify and exploit vulnerabilities. Their goal is to provide a realistic assessment of your organization’s susceptibility to attack.
Think of it like this: if your house alarm system is supposed to protect you, the Red Team is the professional burglar hired to try and bypass it. Their success (or failure) reveals the true effectiveness of your security measures.
The Purple Team: Bridging the Gap in Pentesting Security Audits
So, you have a Red Team attacking and a Blue Team defending. But what happens after the attack? That’s where the Purple Team comes in. The Purple Team acts as a bridge between the Red and Blue Teams, facilitating communication and knowledge sharing. They ensure that the Blue Team learns from the Red Team’s findings and improves their defensive capabilities.
Why is a Purple Team Important?
Without a Purple Team, the Red Team’s findings might not be effectively translated into actionable improvements. The Purple Team helps the Blue Team understand the vulnerabilities that were exploited, the techniques used by the Red Team, and how to prevent similar attacks in the future. It’s all about continuous improvement.
Consider these benefits of a Purple Team approach:
- Improved communication between Red and Blue Teams
- Enhanced knowledge sharing
- Faster remediation of vulnerabilities
- Stronger overall security posture
- More effective training for the Blue Team
Implementing a Successful Pentesting Security Audit Program in 2024
Implementing a successful pentesting and security audit program requires careful planning and execution. It’s not just about hiring a Red Team and hoping for the best. You need to define clear objectives, establish a well-defined scope, and ensure that the results are used to drive meaningful improvements.
Key Considerations for 2024
In 2024, several factors are particularly important to consider when planning your pentesting and security audit program:
- Cloud Security: Ensure your cloud environments are adequately protected.
- Remote Work: Address the security challenges posed by remote work arrangements.
- Supply Chain Security: Assess the security of your third-party vendors.
- Emerging Technologies: Stay ahead of the curve by testing the security of new technologies like AI and IoT.
Choosing the Right Pentesting Security Audit Partner
Selecting the right pentesting partner is crucial for the success of your program. Look for a provider with a proven track record, experienced pentesters, and a commitment to ethical hacking practices. Ask for references and review their past reports to get a sense of their capabilities.
FAQ: Pentesting Security Audit, Red Team & Purple Team
What is the difference between a vulnerability assessment and a penetration test?
A vulnerability assessment identifies potential weaknesses, while a penetration test actively exploits those weaknesses to demonstrate their impact.
How often should I conduct a penetration test?
The frequency depends on your risk profile and industry regulations, but generally, at least annually or after significant system changes.
What skills are essential for a Red Team member?
Strong technical skills, creativity, problem-solving abilities, and a deep understanding of security vulnerabilities and attack techniques.
How can a Purple Team improve my organization’s security?
By facilitating communication and knowledge sharing between Red and Blue Teams, leading to faster remediation and a stronger overall security posture.
What are the key benefits of a security audit?
Identifying security gaps, ensuring compliance, and improving your organization’s overall security posture.